Introduction to DevSecOps on GCP
Part 1 of the DevSecOps CI/CD Series
What is DevSecOps?
DevSecOps is the practice of integrating security into every phase of the DevOps lifecycle, ensuring that security is not an afterthought but a continuous process. Unlike traditional DevOps, where security is often handled at the final stages, DevSecOps follows a "shift-left" approach—meaning security is embedded early in the development pipeline. This proactive strategy reduces vulnerabilities and prevents security issues before they reach production.
Why Security Matters in Modern CI/CD Pipelines
As organizations accelerate software delivery with CI/CD pipelines, security risks have increased. Some common threats include:
- Supply Chain Attacks – Attackers inject malicious code into dependencies.
- Insecure Containers – Misconfigured or outdated container images introduce vulnerabilities.
- Secrets Exposure – Hardcoded credentials or API keys in repositories.
- Insufficient Access Controls – Overprivileged accounts and mismanaged IAM policies.
Real-world incidents, such as the SolarWinds attack and misconfigured cloud storage breaches, highlight the importance of integrating security into CI/CD workflows. Compliance with standards like ISO 27001, SOC 2, and HIPAA further reinforces the need for robust security practices.
How GCP Supports DevSecOps
Google Cloud Platform (GCP) provides native security services that seamlessly integrate with DevOps workflows. Key security features include:
- IAM (Identity and Access Management) – Enforce least privilege access.
- Cloud Build – Secure, auditable build pipelines with automated security scans.
- Artifact Registry – A secure and scalable repository for managing software artifacts, including container images.
- Container Analysis – Automated vulnerability scanning for container images.
- Binary Authorization – Enforces deployment security policies to ensure only trusted, scanned container images are deployed.
- Cloud Security Command Center (SCC) – Centralized security monitoring to detect and mitigate threats.
By leveraging these services, teams can automate security and maintain compliance without slowing down development cycles.
Overview of the DevSecOps Pipeline on GCP
To effectively implement DevSecOps on GCP, security must be embedded at every phase of the CI/CD workflow. Below is a diagram that illustrates a secure DevSecOps pipeline, mapping each step to security controls and best practices.
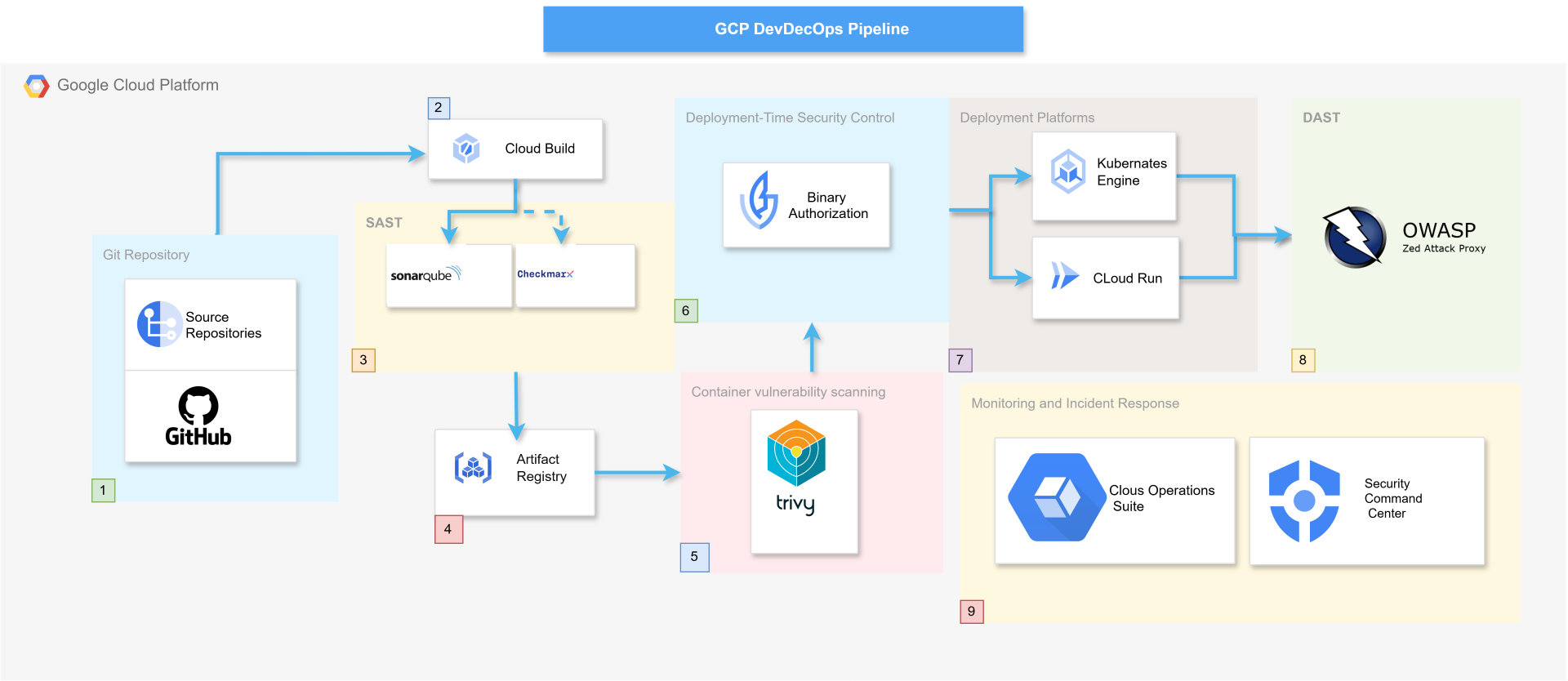
Step-by-Step Breakdown of the DevSecOps Pipeline we will build in this series
1️⃣ Source Code Management
Developers push code to GitHub or Cloud Source Repositories.
Security best practices:
Enforce branch protection rules (e.g., mandatory pull request reviews).
Use secrets scanning to prevent hardcoded credentials.
Implement commit signing for code integrity.
2️⃣ Build & CI/CD Execution with Cloud Build
Cloud Build triggers a CI/CD pipeline when new code is pushed.
Security best practices:
Use private workers to isolate build processes.
Ensure Cloud Build logs are centrally stored for auditing.
Scan dependencies for vulnerabilities in third-party packages.
3️⃣ Static Application Security Testing (SAST)
SonarQube / Checkmarx scan the codebase for vulnerabilities.
Security checks at this stage include:
Detecting SQL injection, XSS, and insecure dependencies.
Enforcing coding standards to prevent security misconfigurations.
4️⃣ Secure Artifact Management
Built artifacts (binaries, container images) are stored in GCP Artifact Registry.
Security measures:
Immutable artifacts to prevent tampering.
Enable vulnerability scanning at rest.
5️⃣ Container Vulnerability Scanning
Trivy scans container images before deployment.
Security best practices:
Automatically block images with critical vulnerabilities.
Ensure minimal base images to reduce the attack surface.
6️⃣ Deployment Security with Binary Authorization
Before deployment, Binary Authorization ensures only signed and verified images are allowed.
Prevents:
Deployment of unverified images.
Running images from unauthorized sources.
7️⃣ Secure Deployment to Kubernetes or Cloud Run
Secure containerized applications are deployed on Google Kubernetes Engine (GKE) or Cloud Run.
Security considerations:
IAM-based access control for deployments.
Least privilege container execution (restrict root user access for example)
8️⃣ Dynamic Application Security Testing (DAST)
OWASP ZAP performs real-time security testing on deployed applications.
Detects injection attacks, misconfigurations, and authentication flaws.
9️⃣ Continuous Monitoring & Incident Response
Cloud Operations Suite (logging, monitoring at least) and Security Command Center (SCC) provide:
Threat detection & security analytics.
Log-based alerts for real-time monitoring.
Compliance monitoring for security posture management.
Introducing the Sample Application
To give this series a practical dimension, we’ll use a small application as a reference throughout the posts. This app will help demonstrate how to apply DevSecOps principles in a real-world scenario—from secure code management to automated testing, deployment, and monitoring using GCP services.
Final Thoughts
This DevSecOps pipeline on GCP ensures security is integrated from development to deployment. Each step minimizes risks while maintaining automation and agility.
In the next post, we will explore Setting Up a Secure GitOps Workflow, focusing on best practices for managing source code securely with GitHub or Cloud Source Repositories. Stay tuned! 🚀